Implementation
Bluetooth uses a radio technology called frequency hopping spread spectrum, which chops up the data being sent and transmits chunks of it on up to 79 bands of 1 MHz width in the range 2402-2480 MHz. This is in the globally unlicensed Industrial, Scientific and Medical (ISM) 2.4 GHz short-range radio frequency band.
Bluetooth is a packet-based protocol with a master-slave structure. One master may communicate with up to 7 slaves in a piconet, all devices share the master's clock. Packet exchange is based on the basic clock, defined by the master, which ticks at 312.5 µs intervals. Two clock ticks make up a slot of 625 µs; two slots make up a slot pair of 1250 µs. In the simple case of single-slot packets the master transmits in even slots and receives in odd slots; the slave, conversely, receives in even slots and transmits in odd slots. Packets may be 1, 3 or 5 slots long but in all cases the master transmit will begin in even slots and the slave transmit in odd slots.
Bluetooth provides a secure way to connect and exchange information between devices such as faxes, mobile phones, telephones, laptops, personal computers, printers, Global Positioning System (GPS) receivers.
The Bluetooth specifications are developed and licensed by the Bluetooth Special Interest Group (SIG). The Bluetooth SIG consists of more than 13,000 companies in the areas of telecommunication, computing, networking, and consumer electronics.
To be marketed as a Bluetooth device, it must be qualified to standards defined by the SIG.
Communication and connection
A master Bluetooth device can communicate with up to seven devices in a Wireless User Group. This network group of up to eight devices is called a piconet. The devices can switch roles, by agreement, and the slave can become the master at any time.
At any given time, data can be transferred between the master and one other device.
The master switches rapidly from one device to another in a round-robin fashion. Simultaneous transmission from the master to multiple other devices is possible via broadcast mode, but not used much.
The Bluetooth Core Specification allows connecting two or more piconets together to form a scatternet, with some devices acting as a bridge by simultaneously playing the master role in one piconet and the slave role in another.
Many USB Bluetooth adapters or "dongles" are available, some of which also include an IrDA adapter. Older (pre-2003) Bluetooth dongles, however, have limited services, offering only the Bluetooth Enumerator and a less-powerful Bluetooth Radio incarnation. Such devices can link computers with Bluetooth, but they do not offer much in the way of services that modern adapters do.
List of applications
- Wireless control of and communication between a mobile phone and a hands free headset This was one of the earliest applications to become popular.
- Wireless networking between PCs in a confined space and where little bandwidth is required.
- Wireless communication with PC input and output devices, the most common being the mouse,keyboard and printer.
- Transfer of files, contact details, calendar appointments, and reminders between devices with OBEX.
- Replacement of traditional wired serial communications in test equipment, GPS receivers, medical equipment, bar code scanners, and traffic control devices.
- For controls where infrared was traditionally used.
- For low bandwidth applications where higher USB bandwidth is not required and cable-free connection desired.
- Sending small advertisements from Bluetooth-enabled advertising hoardings to other, discoverable, Bluetooth devices.
- Wireless bridge between two Industrial Ethernet networks.
- Dial-up internet access on personal computers or PDAs using a data-capable mobile phone as a wireless modem like NOVATEL mifi,
- Short range transmission of health sensor data from medical devices to mobile phones, set top box or dedicated telehealth devices.
Computer requirements
A personal computer that does not have embedded Bluetooth can be used with a Bluetooth adapter or "dongle" that will enable the PC to communicate with other Bluetooth devices (such as mobile phones,mice and keyboards). While some desktop computers and most recent laptops come with a built-in Bluetooth radio, others will require an external one in the form of a dongle.
Unlike its predecessor, IrDA, which requires a separate adapter for each device, Bluetooth allows multiple devices to communicate with a computer over a single adapter.
Operating system support
For Microsoft platforms, Windows XP Service Pack 2 and SP3 releases have native support for Bluetooth 1.1, 2.0 and 2.0+EDR.Previous versions required users to install their Bluetooth adapter's own drivers, which were not directly supported by Microsoft. Microsoft's own Bluetooth dongles (packaged with their Bluetooth computer devices) have no external drivers and thus require at least Windows XP Service Pack 2. Windows Vista RTM/SP1 with the Feature Pack for Wireless or Windows Vista SP2 support Bluetooth 2.1+EDR. Windows 7 supports Bluetooth 2.1+EDR and Extended Inquiry Response (EIR).The Windows XP and Windows Vista/Windows 7 Bluetooth stacks support the following Bluetooth profiles natively: PAN, SPP, DUN, HID, HCRP. The Windows XP stack can be replaced by a third party stack which may support more profiles or newer versions of Bluetooth. The Windows Vista/Windows 7 Bluetooth stack supports vendor-supplied additional profiles without requiring the Microsoft stack to be replaced.
Linux has two popular Bluetooth stacks, BlueZ and Affix. The BlueZ stack is included with most Linux kernels and was originally developed by Qualcomm. The Affix stack was developed by Nokia. FreeBSD features Bluetooth support since its 5.0 release. NetBSD features Bluetooth support since its 4.0 release. Its Bluetooth stack has been ported to OpenBSD as well.
Mobile phone requirements
A Bluetooth-enabled mobile phone is able to pair with many devices. To ensure the broadest support of feature functionality together with legacy device support, the Open Mobile Terminal Platform (OMTP) forum has published a recommendations paper, entitled "Bluetooth Local Connectivity" The Bluetooth SIG Web site offers additional information about use cases for Bluetooth-enabled mobile phones.
Specifications and features
The Bluetooth specification was developed in 1994 by Jaap Haartsen and Sven Mattisson, who were working for Ericsson in Lund, Sweden. The specification is based on frequency-hopping spread spectrum technology.
The specifications were formalized by the Bluetooth Special Interest Group (SIG) . The SIG was formally announced on May 20, 1998. Today it has a membership of over 13,000 companies worldwide. It was established by Ericsson, IBM, Intel, Toshiba, and Nokia , and later joined by many other companies.




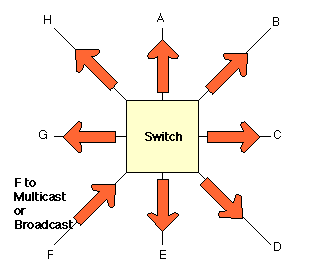
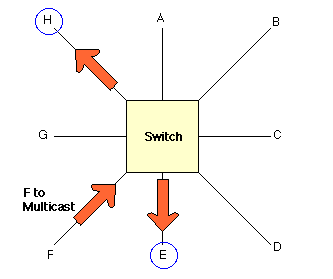

 Ethernet itself is a shared media, so there are rules for sending packets to avoid conflicts and protect data integrity. Nodes on an Ethernet network send packets when they determine the network is not in use. It is possible that two nodes at different locations could try to send data at the same time. When both PCs are transferring a packet to the network at the same time, a collision will result. Both packets are retransmitted, adding to the traffic problem. Minimizing collisions is a crucial element in the design and operation of networks. Increased collisions are often the result of too many users or too much traffic on the network, which results in a lot of contention for network bandwidth. This can slow the performance of the network from the users point of view. Segmenting, where a network is divided into different pieces joined together logically with switches or routers, reduces congestion in an overcrowded network.
Ethernet itself is a shared media, so there are rules for sending packets to avoid conflicts and protect data integrity. Nodes on an Ethernet network send packets when they determine the network is not in use. It is possible that two nodes at different locations could try to send data at the same time. When both PCs are transferring a packet to the network at the same time, a collision will result. Both packets are retransmitted, adding to the traffic problem. Minimizing collisions is a crucial element in the design and operation of networks. Increased collisions are often the result of too many users or too much traffic on the network, which results in a lot of contention for network bandwidth. This can slow the performance of the network from the users point of view. Segmenting, where a network is divided into different pieces joined together logically with switches or routers, reduces congestion in an overcrowded network.